Do any games get hacking right? We ask an actual hacker
Cracking the code

The door to this government facility is locked, and you don't have the futuristic key card! What do you do? Well, in 50% of games, you're given the option to hack the terminal to get inside, because that's what action heroes do when the door is too thick to kick in. Luckily, this is something your character just happens to be adept at.. Cue up hacking mini-game! It's time to connect pipes, link nodes, or do something else that doesn't really remind anyone of hacking. Or, well I don't think it does.
I'm not a hacker (despite what my email address in 1999 might have said), so instead of just swinging my ignorance around, I decided to consult an expert. Our hacker--who prefers to be anonymous, because hackers have a flair for the theatric--has been toying with computers since 1979. He's got plenty of experience in the field, so rest assured he knows what he's talking about as he takes us through gaming's attempts to get hacking right.
Fallout 3
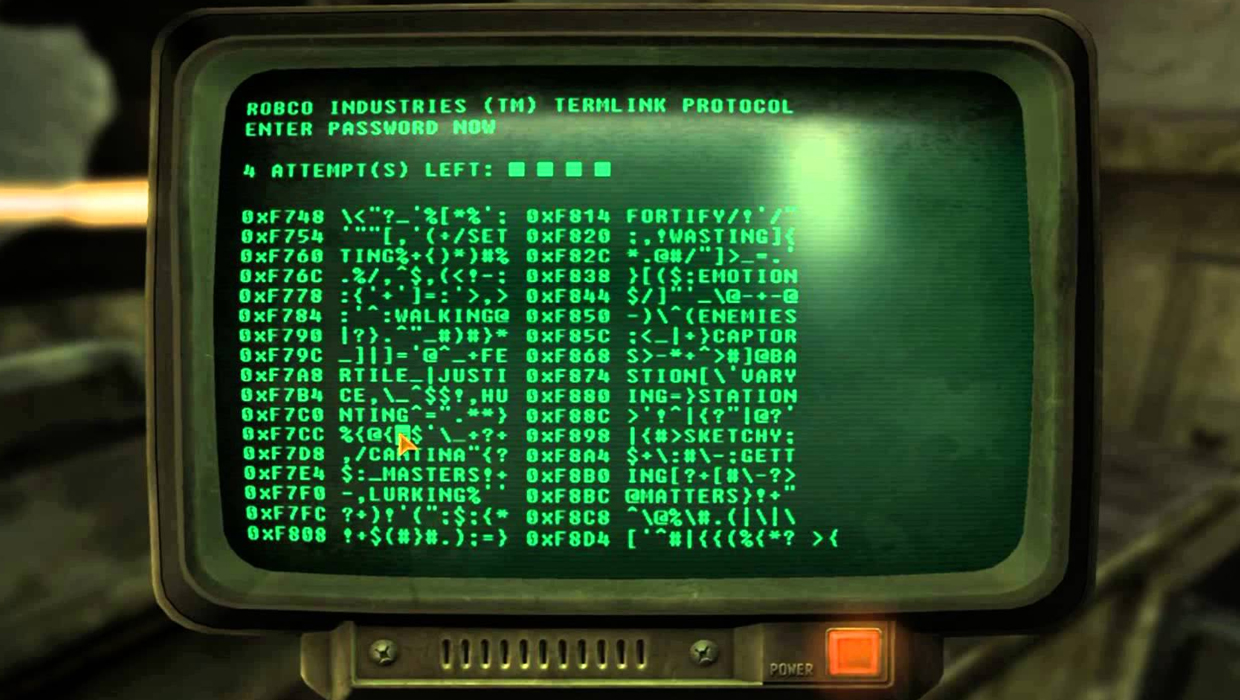
How you hack: Choosing random words on a green computer screen tells you how close you are to the password, but if you screw up too many times the computer locks you out.
Does it make sense? Our hacker said that the computers in Fallout look about as powerful as an Apple II, which would use short, simple passwords--just like the ones in the game. Visually, it's also pretty on-point. "The interface does feel like old school sector scanners which showed the raw information saved in memory or on a disk." he explained. "Most of the memory locations contain symbols or gibberish, but some words do pop up." The notion of there being a limited number of attempts is also correct. "Many systems will lock up the terminal if you guess wrong too many times, and cycling the power may or may not work to reset those numbers." The main problem arises when the system tells the hacker if they are close to right. "How logical would it be to have an advanced computer system tell you the equivalent of 'You are getting warmer' as you attempt to violate the security protocols?"
Alpha Protocol
How you hack: Scrolling through a large field of moving numbers and letters lets you find password, frozen in a field of cycling symbols.
Does it make sense? On the one hand, Alpha Protocol's hacking has the right idea of an end-game: you're trying to find a password, so looking for it amongst bits of code does, technically, make some sort of sense. On the other hand, this isn't actually how it would look. At all. Our hacker says that "the hacking interface involves a flashy word search puzzle on crack being played by someone having a seizure." Searching for a password is smart, but there's no way it would show up in such a flashy display of cycling numbers. "Seriously, what gives with this one? This has about as much to do with hacking as dubstep has to do with Mozart."
BioShock
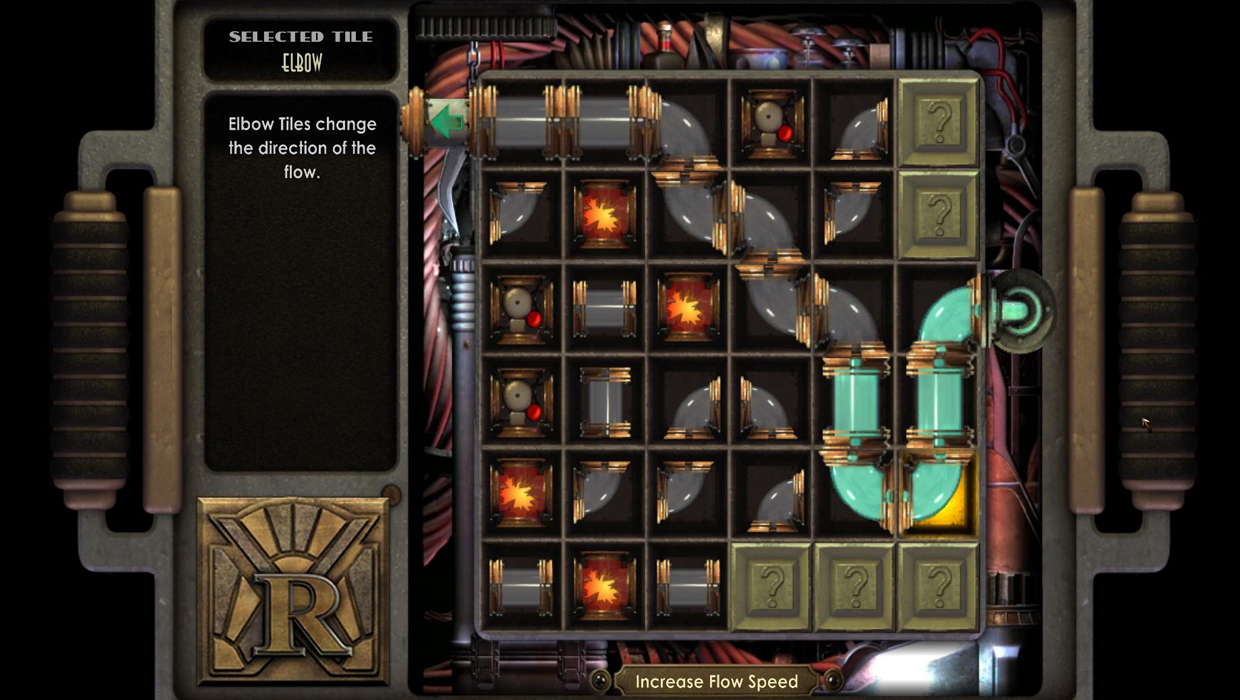
How you hack: Flipping over tiles reveals segments of pipe, which need to be connected to reroute fluid on a grid.
Weekly digests, tales from the communities you love, and more
Does it make sense? More than you might think, actually. Our hacker explained that, within the context of the game's technology (which is mostly steam-based), the Pipe Dreams mini-game has its merits. "If you consider that in an underwater world, the circuitry might be liquid based, that in such a world, rerouting the liquid could change a turret into thinking that what it considered a friend is now a foe, you start to see some twisted logic in what they have presented." It might not fit into the traditional view of hacking (aka, a teenager pounding on a keyboard), but "figuring out ways to repurpose available resources is certainly an acceptable view of hacking."
EVE Online

How you hack: Working through a system of nodes, your goal is to hack into the system to destroy its core in order to loot the data inside.
Does it make sense? Mechanics aside, EVE's hacking is likely the closest in terms of your actual goal: you're not just opening doors or breaking security cameras, you're trying to break into a system for monetary gain. But when it actually comes to the act of hacking, EVE's is more symbolic than anything--you're basically executing a Denial of Service attack. "There are no code or interface similarities to what hacking looks like today. It simulates program-style hacking, where the hacker is using snippets of code or sometimes even full blown programs to breach areas of a computer system." The biggest issue our hacker has with EVE's method is the way in which you stumble onto countermeasures. "Encountering a virus on a foreign system isnt like finding a vicious dog waiting to attack you. It would be more like finding a vial of liquid that would only harm you if you were dumb enough to open and drink it."
Mass Effect
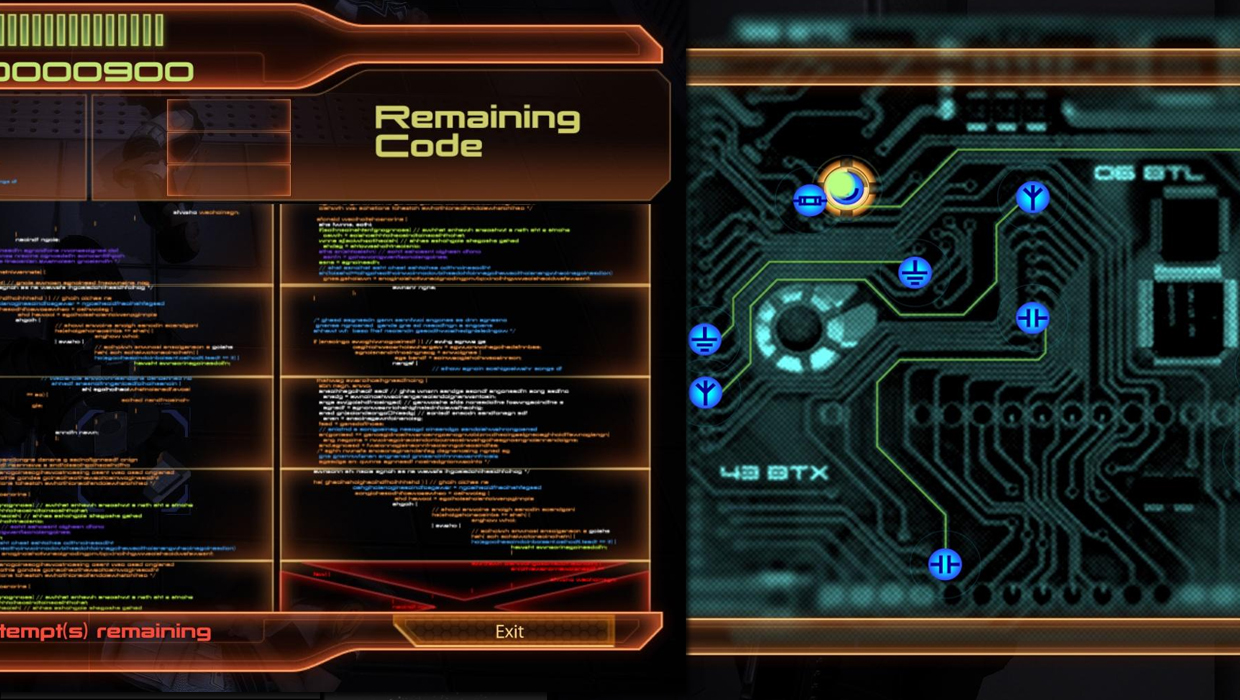
How you hack: ME's hacking comes in multiple flavors. One has you trying to match icons on a circuit board, and the other is about matching snippets of scrolling code.
Does it make sense? The first method, which has you matching contacts, isn't actually that off-base. "This seems like a reasonable assumption for a hardware hack as you are in a sense rewiring the lock, keypad, etc." But while the second method--matching bits of code--might look more realistic, it's actually further away from what hacking really is. "Having the user try to find a snippet of code much too small to read from a picture of that code doesnt relate to anything in the real world, our hacker explained. "The user is also punished when selecting code that is highlighted by a large red X, which also makes no logical sense at all." Again, it goes back to the idea that the people that created these security systems developed some sort of HUD for hackers to use, which simply doesn't happen.
Splinter Cell: Double Agent

How you hack: Find the frozen numbers on the terminal and plug them in as other numbers flash wildly.
Does it make sense? Just as is the case with Alpha Protocol's hacking, which also has you trying to avoid seizures by looking at flashing text, Double Agent misses the mark. "The mini-game itself requires you to find the number that is not constantly changing. Again, no relation to any kind of hacking or coding," he explained, musing that it's not only inaccurate, but it doesn't really seem to be any fun, either. After watching a video which showed Sam Fisher disarming a missile launch, he said that it was "not really a hacking goal in the traditional sense and begs the question: why cant I just smash the launch computer?"
Deus Ex: Human Revolution
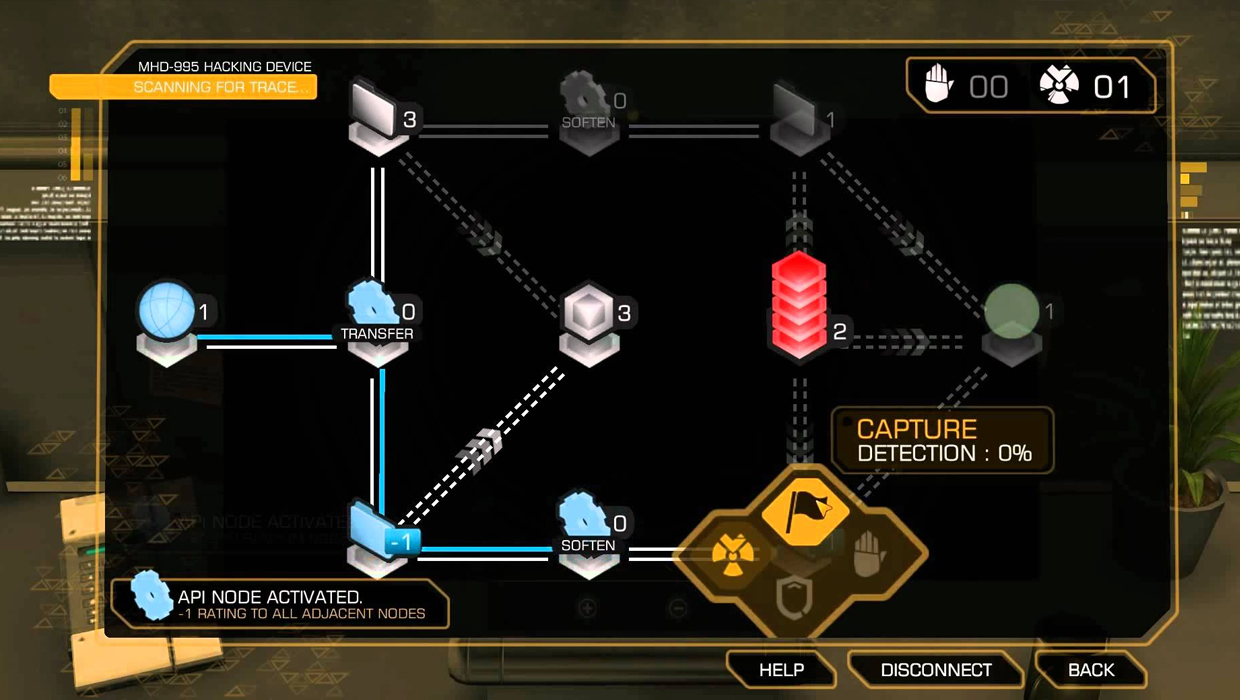
How you hack: You're tasked with capturing points along a web, trying to connect the start and end point before the alarm is raised.
Does it make sense? Like EVE's, Deus Ex's hacking takes the symbolic route, focusing more on network access and node-based networking than program-style hacking. But while this takes place in the future, it uses relatively retro thinking when it comes to its methods. "Although old style computers were connected through token ring or hub and spoke style networks, modern systems (and likely future systems) are almost all peer to peer, meaning you can get to any other system without going through each in turn. It does not make much sense to represent computer security as a sequence of nodes that must be compromised in sequence." What it gets right, though, is that unsuccessful attempts can set off alarms, especially since you're often hacking security systems.
Uplink
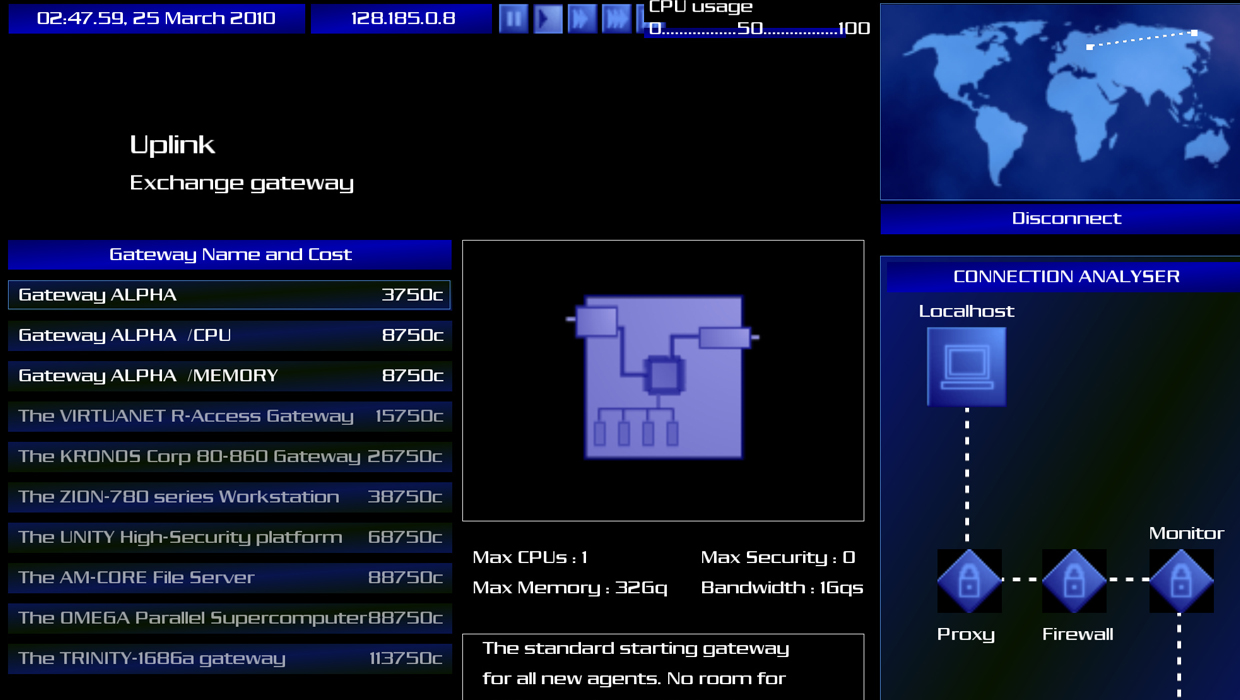
How you hack: Transfer funds from different bank systems into your account by hacking proxies, IPs, and a bunch of other things Hollywood says you're supposed to do while hacking.
Does it make sense? Uplink definitely provides the most complicated hacking experience. Many point at it as the hacking game, but our expert isn't convinced. "The game starts off with you having the account number and password of the account you are going to steal from?" he laughs. "If you have that, why then are we going to hack the account?" Once you find a bank, you bypass the proxy server (which he says makes no sense as it does nothing to get you into their system) and transfer money to the IP address of your local bank (which doesn't work that way). "This game is meant to feel like hacking, and it does use some terminology and references that are techy, but its not very close to the real thing. Its the Easy Bake oven approach to fine dining. Yes it can cook, but thats about as far as the similarities go."
It's in the code
I obviously need to thank our anonymous hacker for helping out on this feature, otherwise I'd be comparing the cycling numbers of Alpha Protocol to the scene in Swordfish where the guy who plays Hugh Jackman types fast on a keyboard while a woman tries to erm distract him. That, or I'd have to just watch the movie Wargames over and over again, which doesn't sound that bad, actually.
And if you're interested in more, check out a metalworker weighs in on the most impractical armor and the craziest RPG weapons.
Hollander Cooper was the Lead Features Editor of GamesRadar+ between 2011 and 2014. After that lengthy stint managing GR's editorial calendar he moved behind the curtain and into the video game industry itself, working as social media manager for EA and as a communications lead at Riot Games. Hollander is currently stationed at Apple as an organic social lead for the App Store and Apple Arcade.



